
Overview
Code review processes include spotting potential vulnerabilities in a software’s code during the early stages of the Software Development Life Cycle (SDLC). The guidelines were benchmarked against the Open Worldwide Application Security Project Code Review Guidelines to meet international standards. Through this, software developers and engineers can better identify and assess code vulnerabilities, allowing applications to be built in a more secure, robust and more cost-effective manner.
Objective
This code review process ensures that applications are built with security in mind. This reduces the chances of security breaches, data leaks, and other cybersecurity threats.
Scope
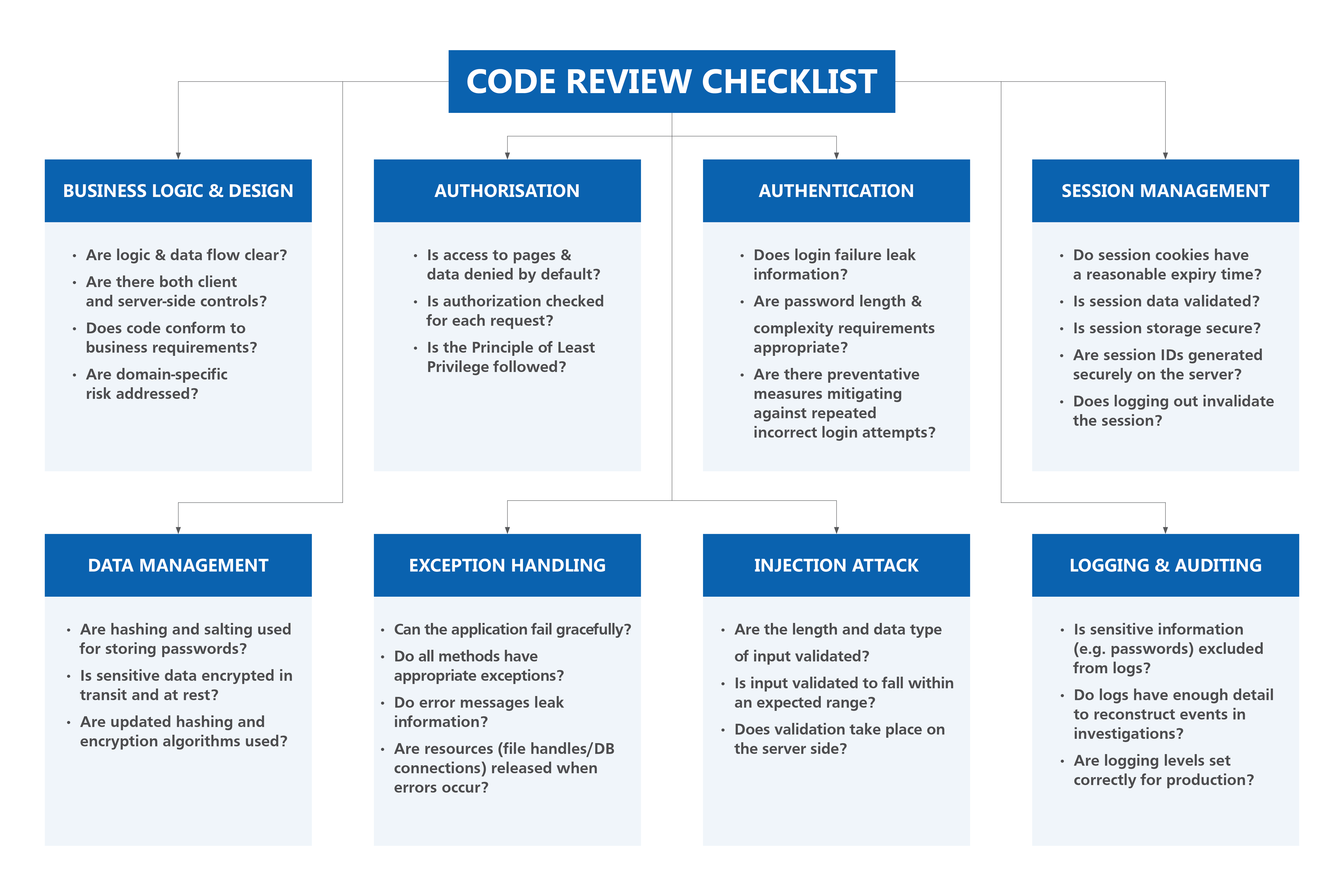
The scope of the secure guidelines for code review processes covers eight key areas. This includes:
- Authentication: preventing malicious users from gaining access to protected functionalities
- Authorisation: preventing malicious users from performing unwanted actions on protected resources
- Business Logic & Design: minimising flaws in application design and implementation that can lead to unintended behaviours
- Data Management: exercising extra precaution such as encryption at rest and in transit to protect sensitive data such as IC numbers
- Exception Handling: proper exception handling can prevent leakage of valuable information
- Injection Attack: preventing malicious users from adding/injecting content into an application to modify its behaviour
- Logging & Auditing: application log messages are important for auditing purposes
- Session Management: improper session management can lead to malicious users impersonating others and gaining access to privileged data or application functions
Target Audience and Adoption Criteria
These guidelines are applicable to software developers, engineers, and code reviewers.
Standards, Guidelines and Assessment Criteria
For a summarised checklist of the secure code review process, you may refer to the diagram below.
For more guidelines on the code reviewing process within the Goverment, click here.
Contact Information
Please fill up this form if you have further queries.
Last updated 12 October 2023
Thanks for letting us know that this page is useful for you!
If you've got a moment, please tell us what we did right so that we can do more of it.
Did this page help you? - No
Thanks for letting us know that this page still needs work to be done.
If you've got a moment, please tell us how we can make this page better.

